It can be tricky to grant a new user proper permissions on a secure cluster, let's walk through the steps to enable any new user for table creation on a kerberized cluster. Depends on your cluster size, creating user and group on each node can be tedious. Here we use pssh (Parallel ssh) for this task.
1. Install the tool and prepare a file which contains all your hosts.
For Mac user:
$ brew install psshFor Debian or Ubuntu user:
$ sudo apt-get install pssh
$ cat ~/Documents/nodeshue.txt
hue-1.test.cloudera.com
hue-2.test.cloudera.com
hue-3.test.cloudera.com
hue-4.test.cloudera.com
2. Run follow commands to create user: t1 and group: grp1 on your cluster:
$ pssh -h ~/Documents/nodeshue.txt -i useradd t1
[1] 13:58:48 [SUCCESS] hue-1.test.cloudera.com
[2] 13:58:48 [SUCCESS] hue-2.test.cloudera.com
[3] 13:58:48 [SUCCESS] hue-3.test.cloudera.com
[4] 13:58:48 [SUCCESS] hue-4.test.cloudera.com
$ pssh -hosts ~/Documents/nodes.txt -i groupadd grp1
[1] 13:59:20 [SUCCESS] hue-1.test.cloudera.com
[2] 13:59:20 [SUCCESS] hue-2.test.cloudera.com
[3] 13:59:20 [SUCCESS] hue-3.test.cloudera.com
[4] 13:59:20 [SUCCESS] hue-4.test.cloudera.com
$ pssh -hosts ~/Documents/nodes.txt -i usermod -a -G grp1 t1
[1] 13:59:28 [SUCCESS] hue-1.test.cloudera.com
[2] 13:59:28 [SUCCESS] hue-2.test.cloudera.com
[3] 13:59:28 [SUCCESS] hue-3.test.cloudera.com
[4] 13:59:28 [SUCCESS] hue-4.test.cloudera.com
3.Create same Hue user: t1 and group: grp1 and make “t1” a member of “grp1”.
4.Then log in as any user with sentry admin permission to run following queries in hive editor:
create role write_role;
GRANT ROLE write_role TO GROUP grp1;
GRANT ALL ON SERVER server1 TO ROLE write_role;
Now “t1” user or any user in “grp1” can log in and create table by running any hive/impala DDL queries or through Hue importer.
But mostly we would like to grant proper permissions for users instead of “ALL” on “server”. let's walk through two other examples like read_only_role and read_write_role for specific databases.
Using similar commands to create t2 user in group grp2 and t3 user in group grp3 on cluster and Hue. Then use following statements to grant proper permission to each group:
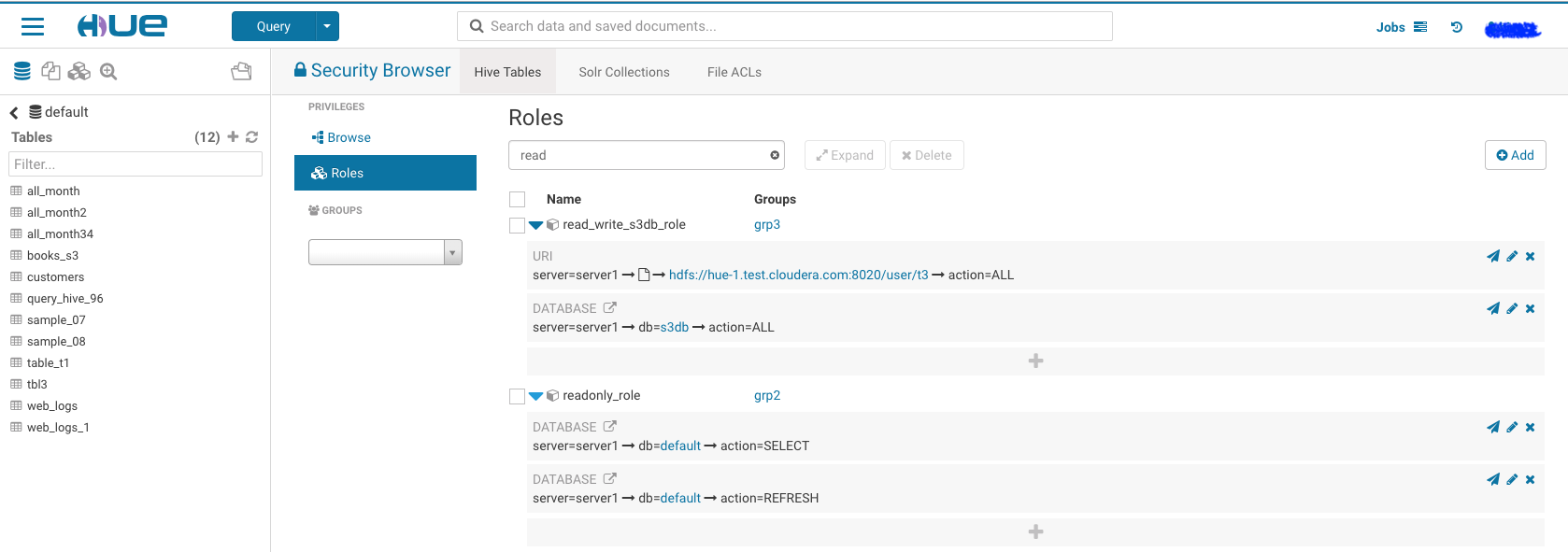
1.Read write access to database: ‘s3db’ for any user in group ‘grp3’:
create role read_write_s3db_role;
GRANT ROLE read_write_s3db_role TO GROUP grp3;
GRANT ALL ON DATABASE s3db TO ROLE read_write_s3db_role;
GRANT ALL ON URI 'hdfs://hue-1.test.cloudera.com:8020/user/t3' to ROLE read_write_s3db_role;
- Read only permission for database: ‘default’ for any user in group ‘grp2’:
create role read_only_defaultDb_role;
GRANT ROLE read_only_defaultDb_role TO GROUP grp2;
GRANT SELECT ON DATABASE default TO ROLE read_only_defaultDb_role;
GRANT REFRESH ON DATABASE default TO ROLE read_only_defaultDb_role;
Now ‘t3’ user can read and create new tables in database:s3db while ‘t2’ user can read database: default only.
We can grant those permission through Hue security page too, it should ends like following.
Note: You have to grant URI permission to avoid following error during table creation:
Error while compiling statement: FAILED: SemanticException No valid privileges User t3 does not have privileges for CREATETABLE The required privileges: Server=server1->URI=hdfs://hue-1.gce.cloudera.com:8020/user/t3/t3_dir->action=*->grantOption=false;
As always please feel free to reach out for any question or feedback!