With the latest release of Hue 3.9, we've added an additional layer of monitoring for Hue administrators.
Hue user administration operations can now be audited and written to a configurable audit log. Administrators can then use Cloudera Navigator's Auditing Component to view, search, filter, and generate reports on these audited events.
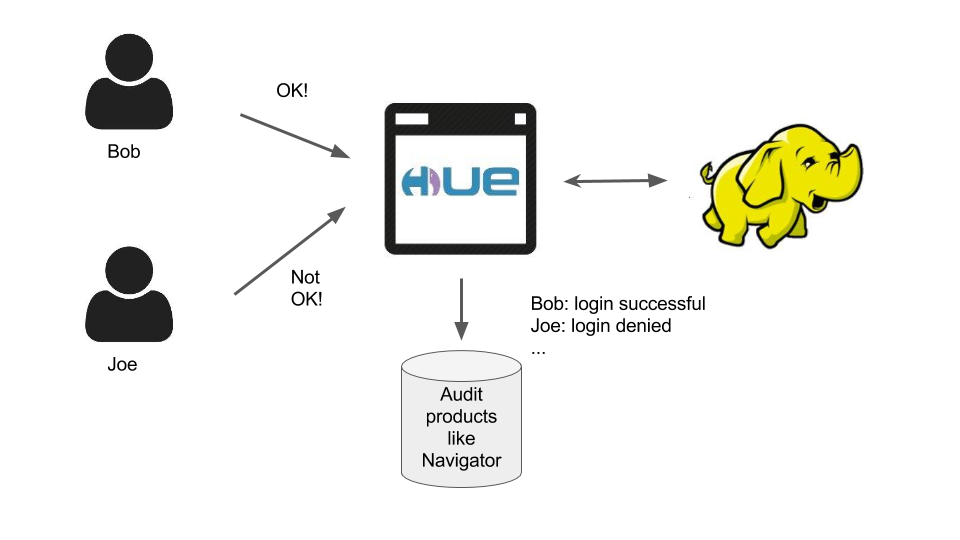
Hue admins can thus easily monitor superuser operations such as adding/editing users and groups, editing permissions, and user logins/logouts. Most importantly, admins can easily detect when unauthorized attempts at these operations have been made, and capture the related metadata for those unauthorized attempts.
To enable and configure the log file used for the audit log, there are 2 new configuration properties that have been added to the hue.ini file, and can be overridden in Cloudera Manager's Service Access Audit Log Properties controls.
[desktop]
\# The directory where to store the auditing logs. Auditing is disable if the value is empty.
\# e.g. /var/log/hue/audit.log
audit_event_log_dir=/Users/jennykim/Dev/hue/logs/audit.log
\# Size in KB/MB/GB for audit log to rollover.
audit_log_max_file_size=100MB
After configuring the audit log and restarting Hue, you can then start viewing the audited operations by tailing the log:
$ tail logs/audit.log
{"username": "admin", "impersonator": "hue", "eventTime": 1447271632364, "operationText": "Successful login for user: admin", "service": "accounts", "url": "/accounts/login/", "allowed": true, "operation": "USER_LOGIN", "ipAddress": "127.0.0.1"}
{"username": "admin", "impersonator": "hue", "eventTime": 1447271704937, "operationText": "Created Group: admins, with member(s): jennykim, admin, hue", "service": "useradmin", "url": "/useradmin/groups/new", "allowed": true, "operation": "CREATE_GROUP", "ipAddress": "127.0.0.1"}
{"username": "admin", "impersonator": "hue", "eventTime": 1447271778278, "operationText": "Created Group: readonly, with member(s): ", "service": "useradmin", "url": "/useradmin/groups/new", "allowed": true, "operation": "CREATE_GROUP", "ipAddress": "127.0.0.1"}
{"username": "admin", "impersonator": "hue", "eventTime": 1447271788277, "operationText": "Successfully edited permissions: useradmin/access", "service": "useradmin", "url": "/useradmin/permissions/edit/useradmin/access", "allowed": true, "operation": "EDIT_PERMISSION", "ipAddress": "127.0.0.1"}
Each audited record contains fields for:
- username of the user executing the action
- impersonator user (always “hue” in this case)
- eventTime in milliseconds since epoch
- allowed, true if operation was authorized, false otherwise
- operation (e.g. - USER_LOGIN, CREATE_USER, CREATE_GROUP, EDIT_PERMISSION, etc.)
- operationText, descriptive text of the operation
- service
- url
- ipAddress of client
Currently, Hue audits the following authentication and useradmin actions:
- USER_LOGIN, USER_LOGOUT
- CREATE_USER, DELETE_USER, EDIT_USER
- CREATE_GROUP, DELETE_GROUP, EDIT_GROUP
- ADD_LDAP_USERS, ADD_LDAP_GROUPS, SYNC_LDAP_USERS_GROUPS
- EDIT_PERMISSION
If you are running Hue with Cloudera Enterprise, you can then view and manage the audit report from Cloudera Navigator and filter on the Service Name for Hue, in this case “HUE-1”:
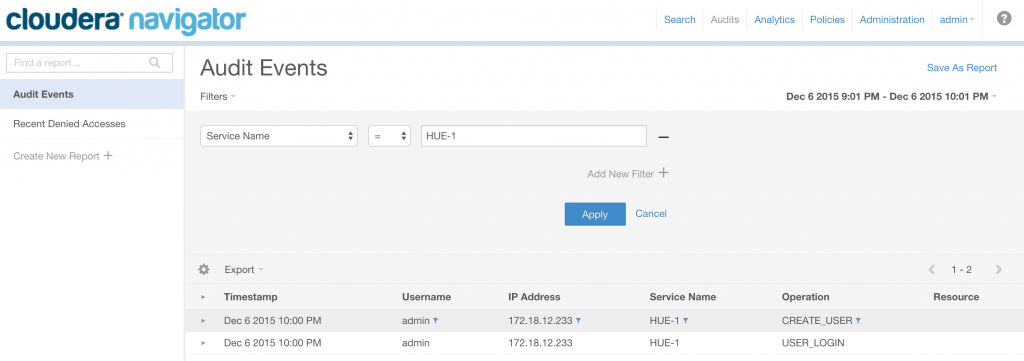
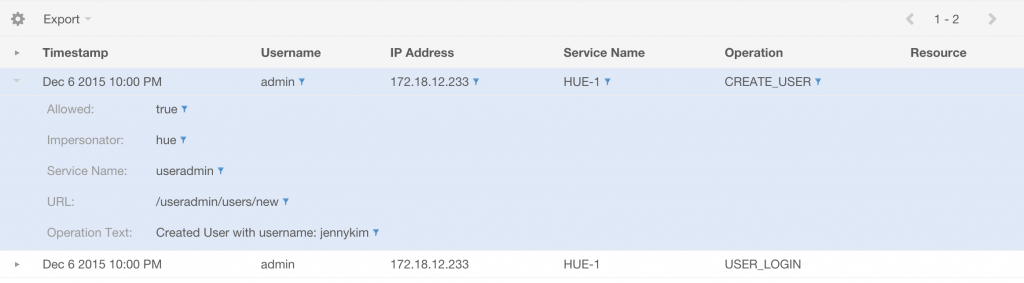
You can expand any audit record to view the metadata for a given operation, including whether it was allowed/authorized, the impersonated user and additional details specific to the operation.
Hue + Navigator provide rich data discovery, audit and policy enforcement features and Hue is evolving in a more enterprise compliance friendly product. If you have any questions, feel free to comment here or on the hue-user list or @gethue!
